Inside the British military base where young hackers learn to stop cybercrime | UK security and counter-terrorism | The Guardian
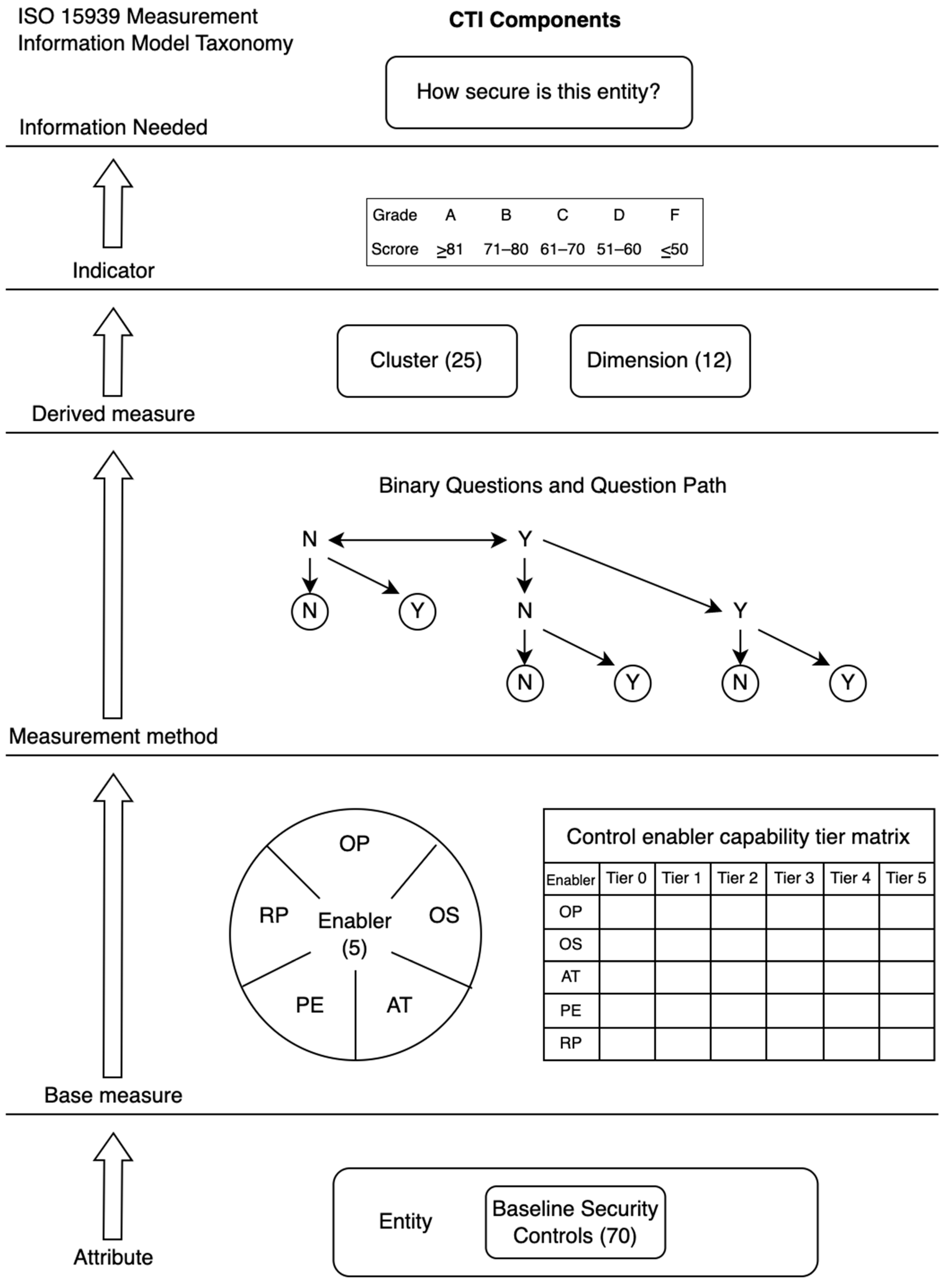
Applied Sciences | Free Full-Text | Cyber Trust Index: A Framework for Rating and Improving Cybersecurity Performance

Cyber Security System Technology Icons Set Vector. Cyber Security Software And Application, Padlock And Password For Data Base And Information Protection From Virus Line. Color Illustrations Stock Vector | Adobe Stock
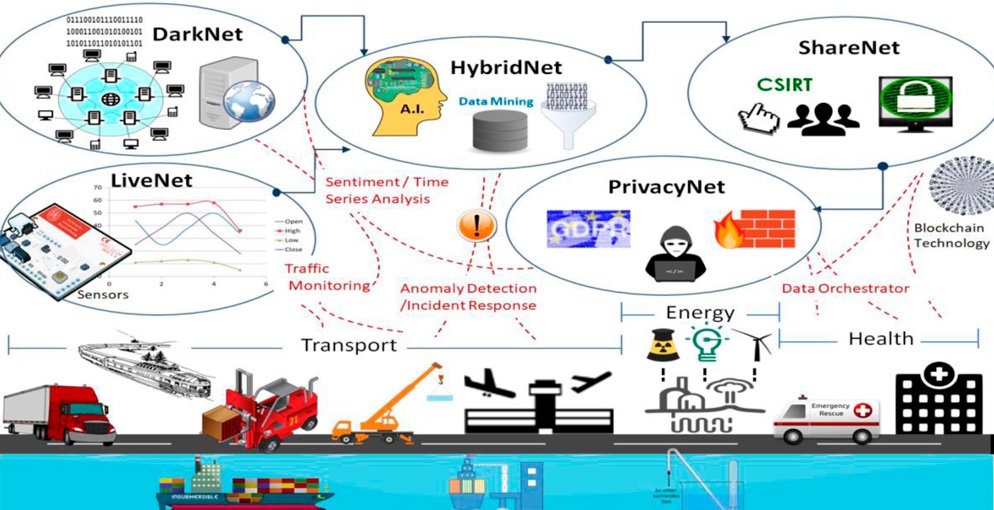
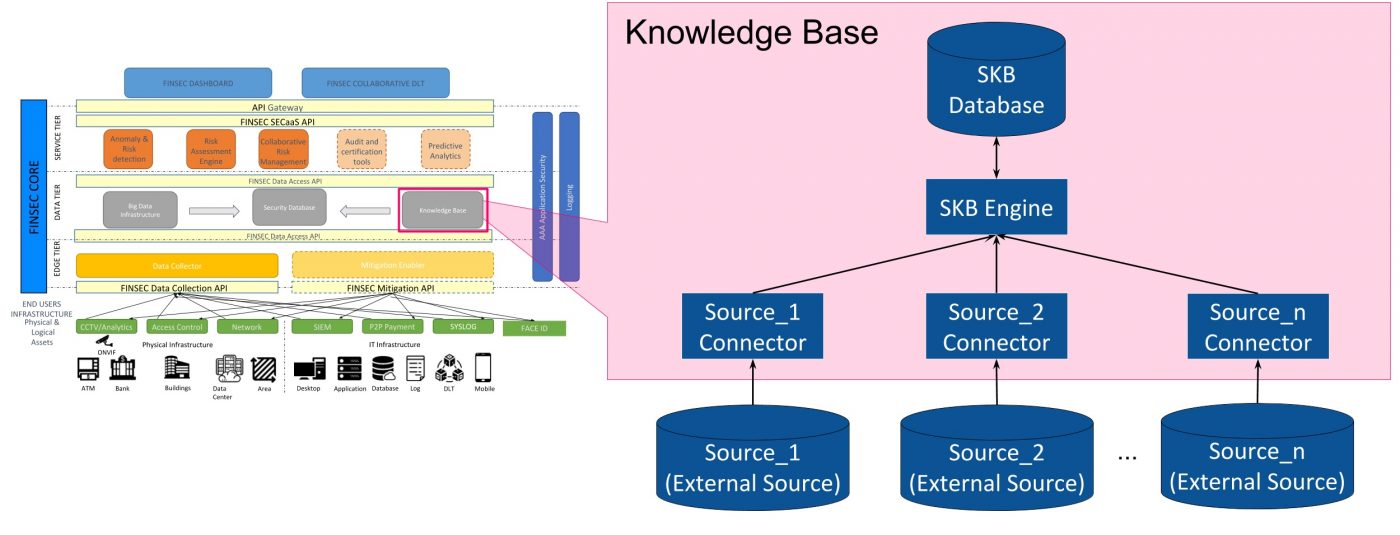
CYBERSANE - CYBER SECURITY INCIDENT HANDLING, WARNING AND RESPONSE SYSTEM FOR THE EUROPEAN CRITICAL INFRASTRUCTURES - Fundación Valenciaport

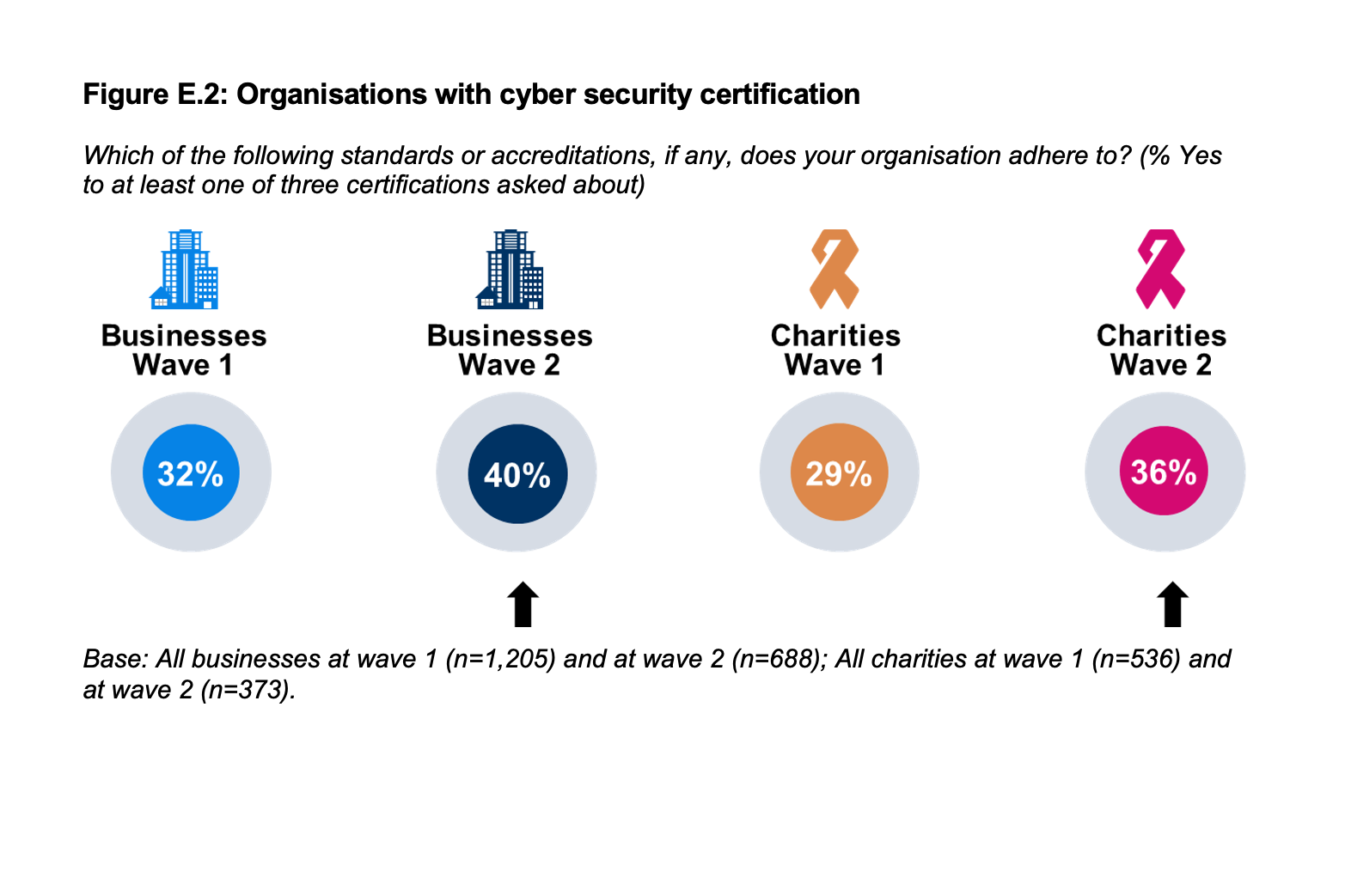
Companies need to invest more in cybersecurity, 5G to propel internet user base to 25 bn in 2023: Rajesh Pant, Government News, ET Government