Countering Swarms: Strategic Considerations and Opportunities in Drone Warfare > National Defense University Press > News Article View

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发
Sustainability | Free Full-Text | State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions

Gotta Catch 'Em All: Understanding How IMSI-Catchers Exploit Cell Networks | Electronic Frontier Foundation

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发
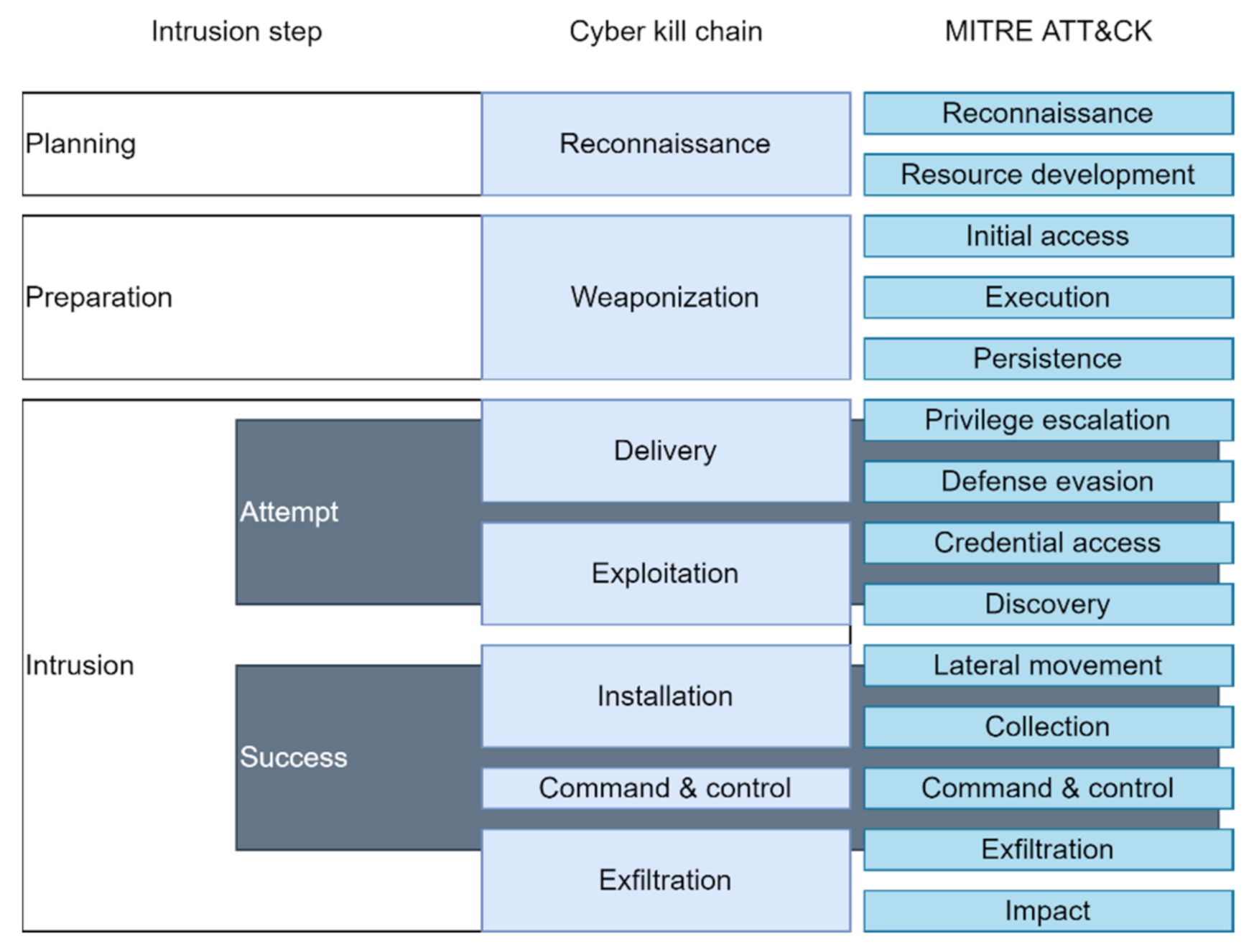
Sensors | Free Full-Text | Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework
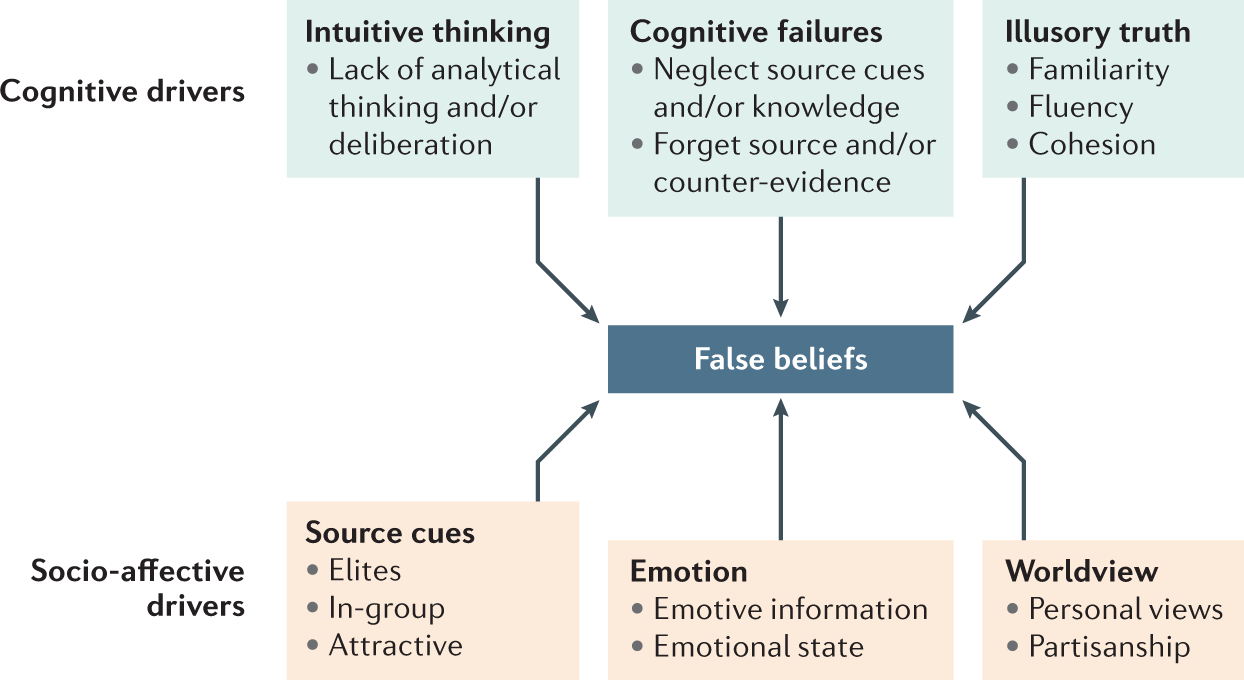
The psychological drivers of misinformation belief and its resistance to correction | Nature Reviews Psychology













![Inside Radio: An Attack And Defense Guide [PDF] [4223clofej90] Inside Radio: An Attack And Defense Guide [PDF] [4223clofej90]](https://vdoc.pub/img/crop/300x300/7h70qulend40.jpg)