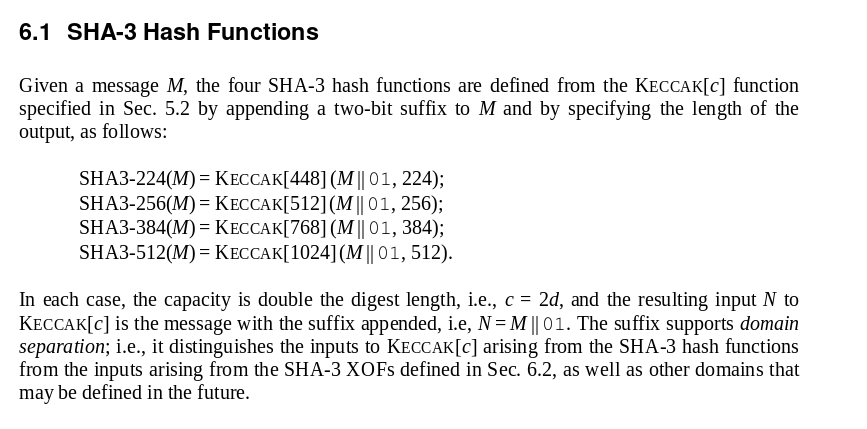
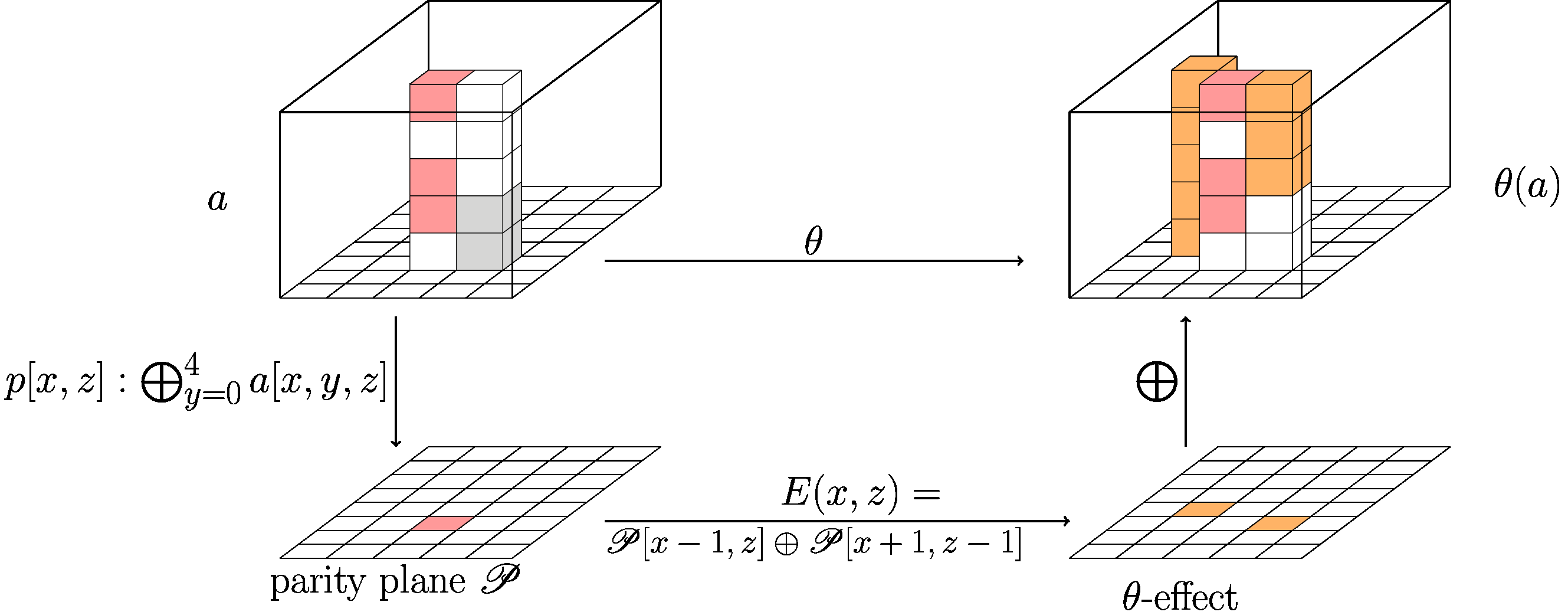
Online SHA-3 Keccak calculator Secure Hash Algorithm 3 Keccakf Keccak-f Keccak512 SHA-2 MD5 FIPS PUB 202 FIPS202

PDF) A Lightweight Implementation of Keccak Hash Function for Radio-Frequency Identification Applications
GitHub - tzumby/ex_keccak: Elixir library for computing Keccak SHA3-256 hashes using a NIF built tiny-keccak Rust crate.
Why Change The Ethereum Classic Proof of Work Algorithm to Keccak-256 (SHA3) | by ETC Cooperative | Ethereum Classic Cooperative | Medium

Figure 4 from Efficient hardware implementations of high throughput SHA-3 candidates keccak, luffa and blue midnight wish for single- and multi-message hashing | Semantic Scholar

PDF) A Lightweight Implementation of Keccak Hash Function for Radio-Frequency Identification Applications
ECIP-1049: Change the ETC Proof of Work Algorithm to Keccak-256 · Issue #13 · ethereumclassic/ECIPs · GitHub
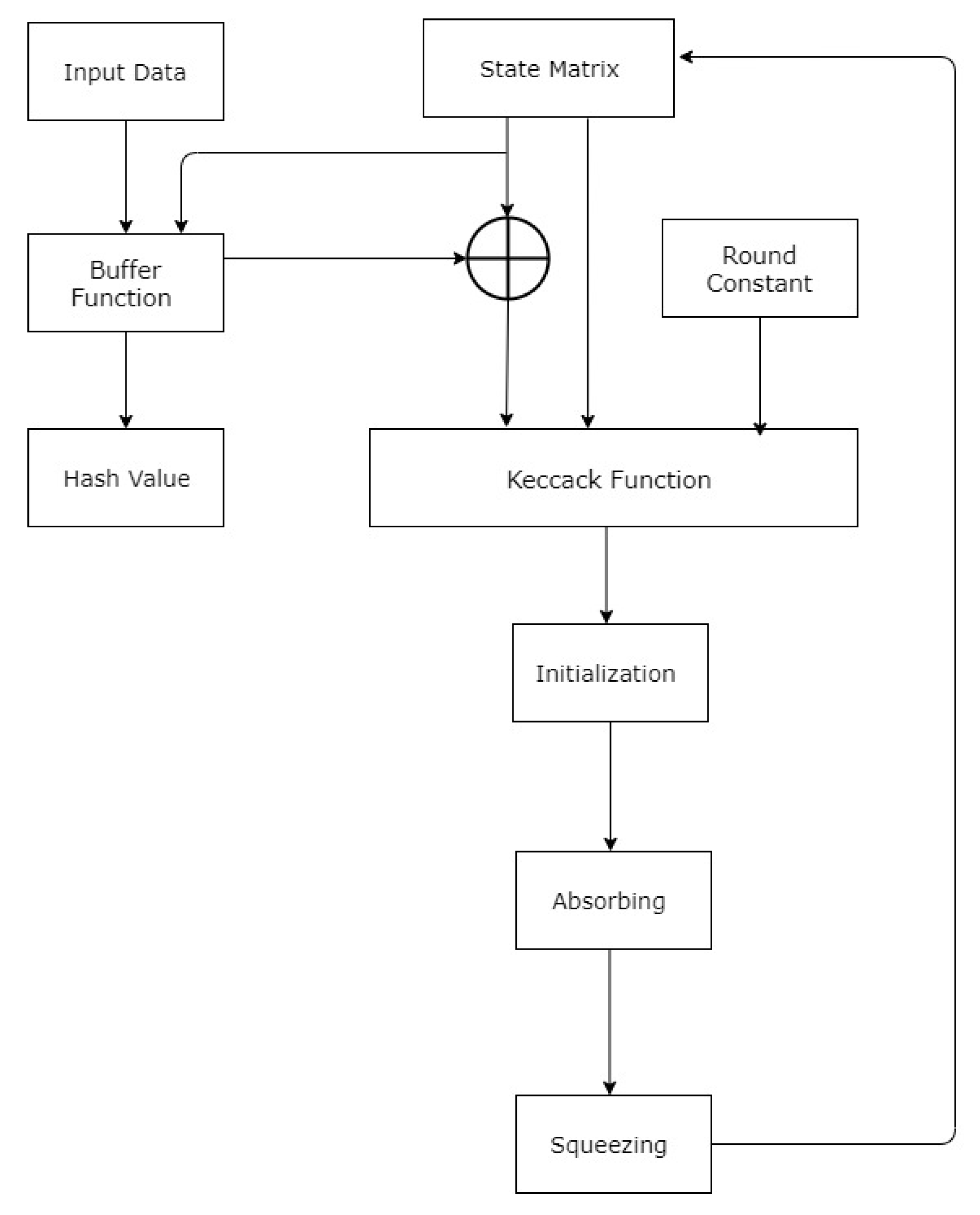
Technologies | Free Full-Text | High Throughput Implementation of the Keccak Hash Function Using the Nios-II Processor


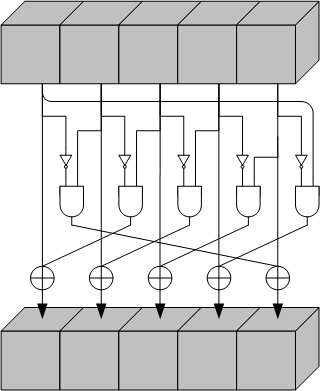
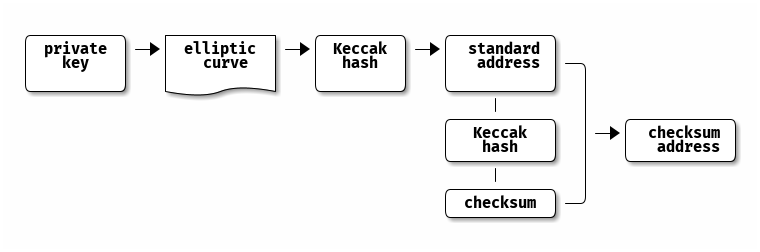





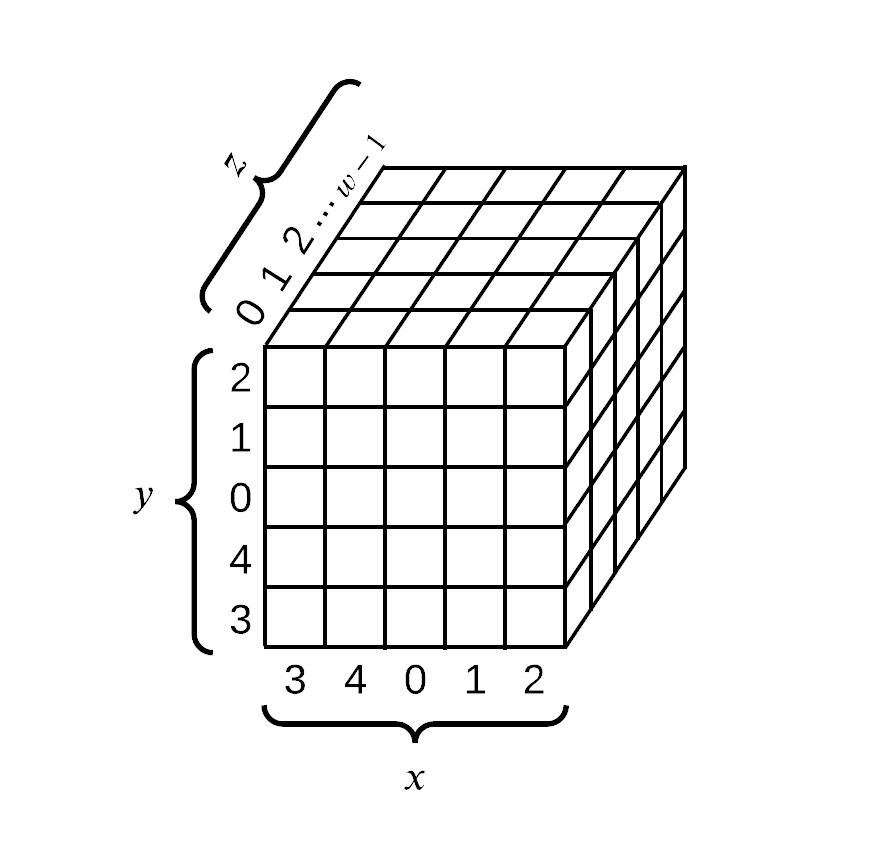

![PDF] Single-Trace Attacks on Keccak | Semantic Scholar PDF] Single-Trace Attacks on Keccak | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9ee36cd01b777000669f94f224e0da57c8e5bcde/26-Figure6-1.png)