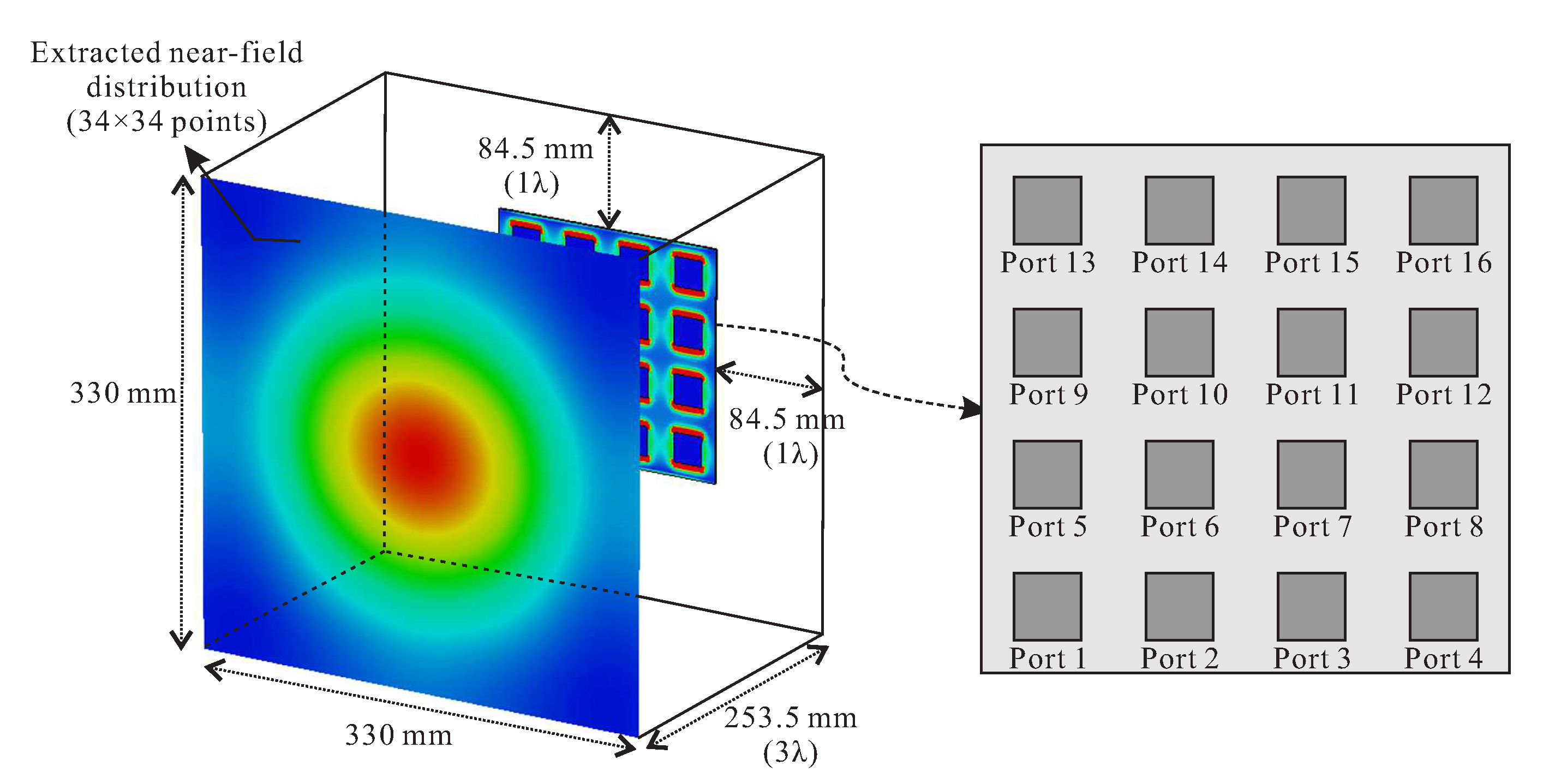
Applied Sciences | Free Full-Text | Near-Field-Based 5G Sub-6 GHz Array Antenna Diagnosis Using Transfer Learning | HTML
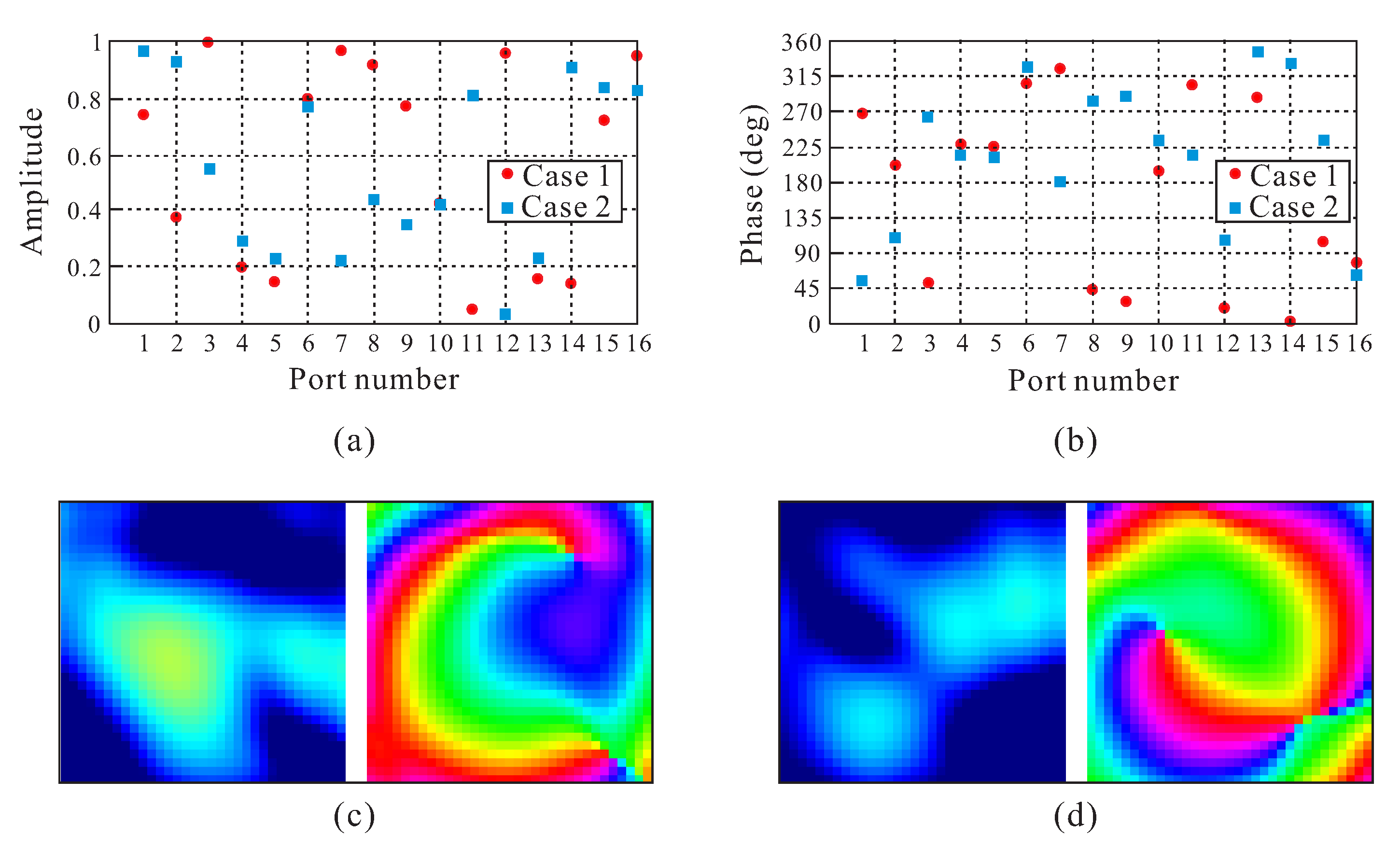
Applied Sciences | Free Full-Text | Near-Field-Based 5G Sub-6 GHz Array Antenna Diagnosis Using Transfer Learning | HTML

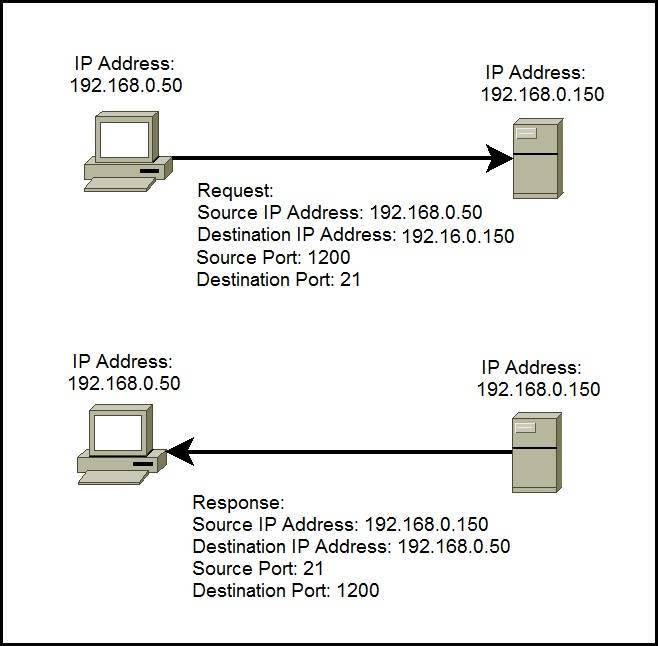
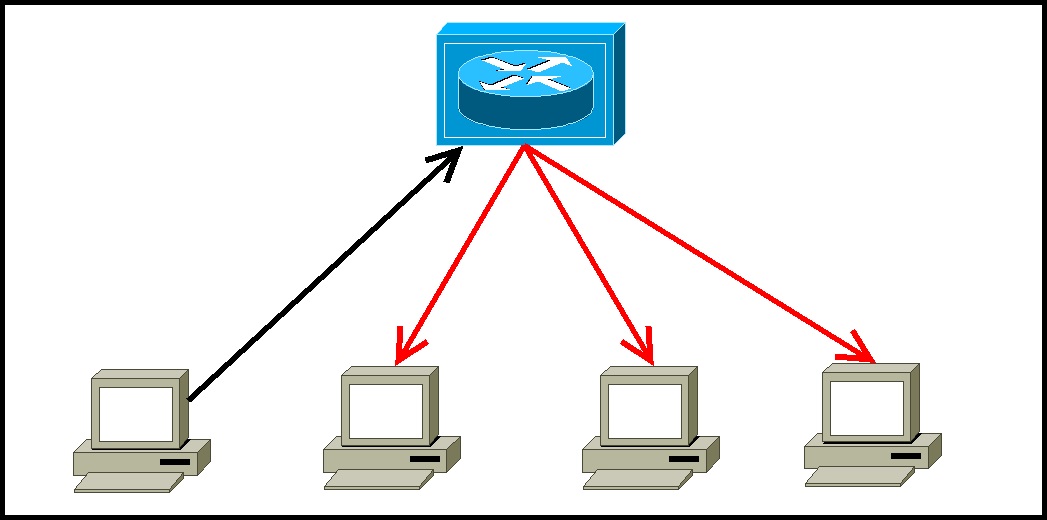
Knock, knock, log: Threat analysis, detection & mitigation of covert channels in syslog using port scans as cover - ScienceDirect
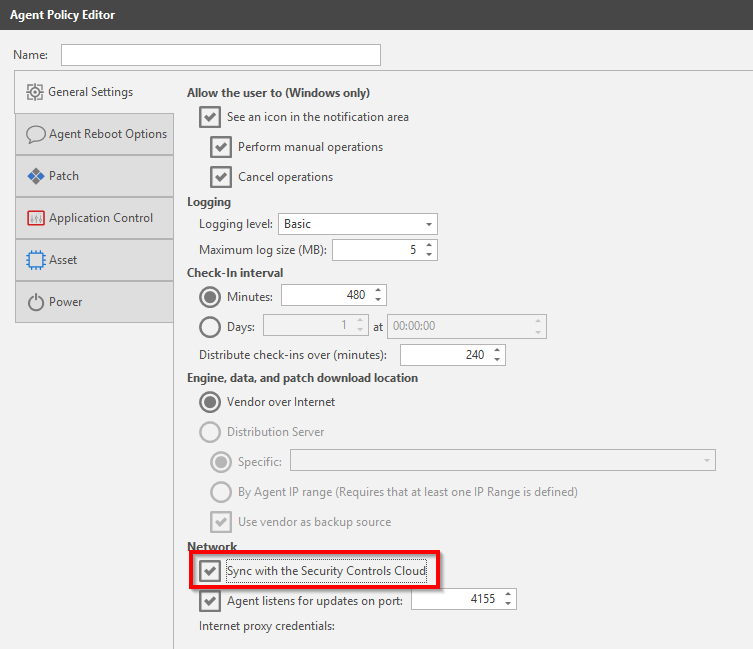
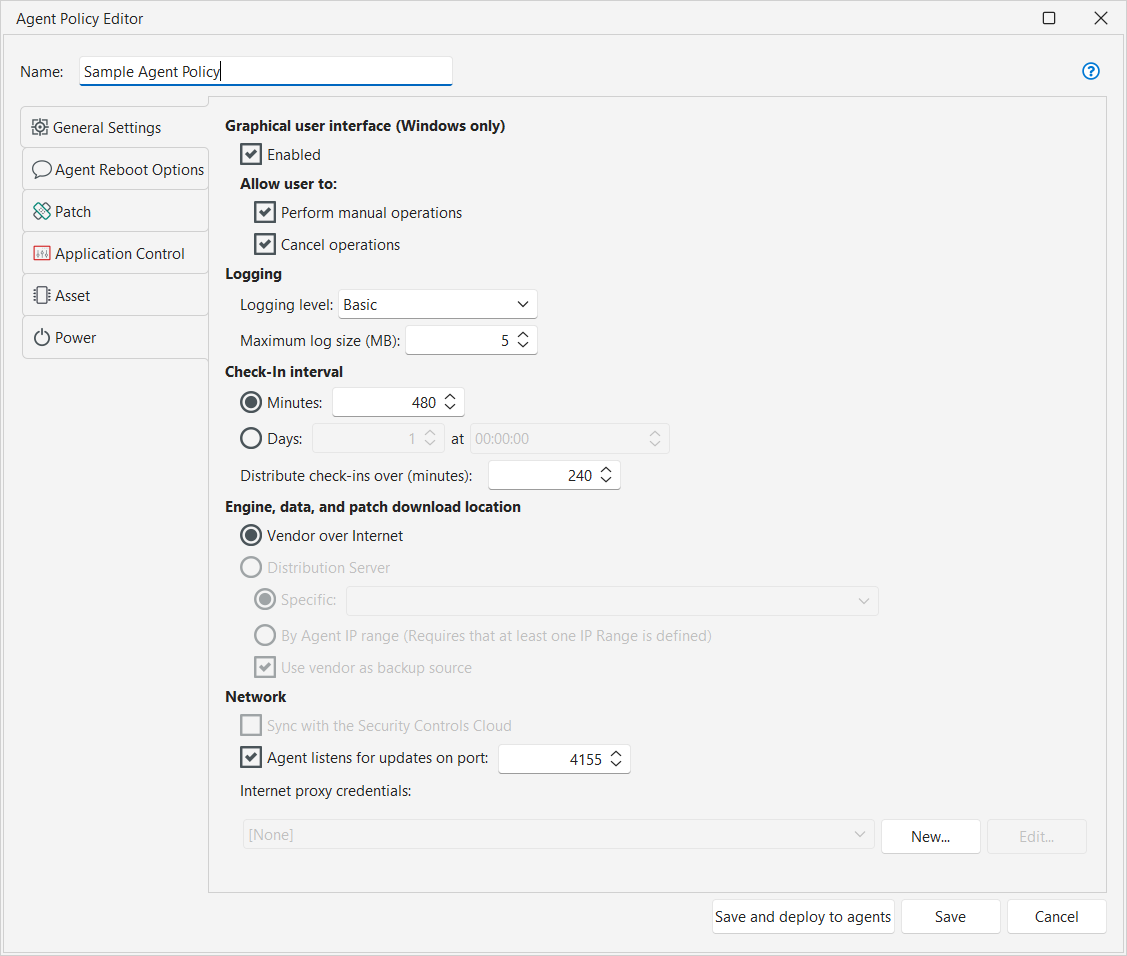
Patching Third-Party Applications Automatically with Ivanti Security Controls - Naglestad Consulting